cnPilot E-Series 4.2.3 has been released. System Release 4.2.3 is a maintenance release on System Release 4.2.2 along with one new feature and additional bug fixes.
Downloads are available for:
Cambium Traffic Class support
Cambium Traffic Class attributes are supported for wireless guest clients. Access point (AP) allows guest clients to communicate destinations (defined using IP/Network address) defined under traffic class names without completing the guest authentication. The RADIUS server can push traffic class name and data quota as part of the RADIUS accept packet or COA update. AP keeps track of guest clients traffic usage against each traffic class and data utilization information is sent to the accounting server in RADIUS accounting packets (Account-Interim update and account stop messages).
Traffic class can be defined under the WLAN profile and only 3 traffic classes are supported via CLI mode only. If APs are managed from cnMaestro, traffic class can be configured in AP Group using User-Defined Overrides options. When the traffic class quota gets exhausted, user clients are redirected to the external captive portal server.
Cambium Networks Wi-Fi devices support the following Cambium vendor-specific (VSA 17713) Traffic Class attributes:
| Name | Number | Type |
|---|---|---|
| Cam-Vlan-Pool-Id | 157 | string |
| CAMB-Authorize-Classes | 158 | tlv |
| CAMB-Authorize-Class-Name | 158.1 | string |
| CAMB-Authorize-Bytes-Left | 158.2 | integer64 |
| CAMB-Traffic-Classes-Acct | 159 | tlv |
| CAMB-Acct-Class-Name | 159.1 | string |
| CAMB-Acct-Input-Octets | 159.2 | integer64 |
| CAMB-Acct-Output-Octets | 159.3 | integer64 |
| CAMB-Acct-Input-Packets | 159.4 | integer64 |
| CAMB-Acct-Output-Packets | 159.5 | integer64 |
| CAMB-Walled-Garden-State | 160 | integer |
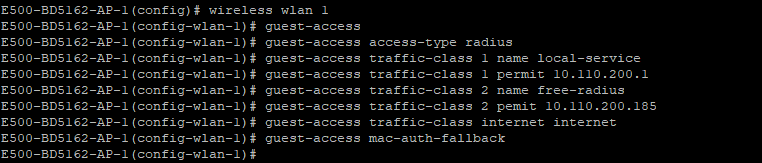
CLI configuration:
Enhancements
| Tracking | Product | Description |
|---|---|---|
| FLCN-11306 | All | RADIUS-based Challenge Handshake Authentication Protocol (CHAP) support is added. |
Fixed issues
| Tracking | Product | Description |
|---|---|---|
| FLCN-12708 | All | MAB feature was not working if the MAC address of the client started with 0. |
| FLCN-12514 | All | Sanitize ping host argument in device-agent. |
| FLCN-12503 | All | AP UI login did not allow 32 characters password. |
| FLCN-12405 | All | The client device on AP2 was not getting an IP address when L2GRE was enabled on AP2 WLAN. |
| FLCN-12291 | All | Adding an SSH key of more than 512 bits did not work. |
| FLCN-12253 | All | Fixed issues in pushing VLAN ID range from a configuration file to the system bridge interface. |
| FLCN-11851 | All | SCMD process crashed when a non-admin user tried to login. |
| FLCN-11492 | All | RADIUS MAC authentication did not work on 1st WLAN. |
| FLCN-11446 | All | Configured SSH key was missing in APs GUI and CLI after its reboot. |
| FLCN-11401 | All | Fixed an error Invalid firmware file when upgraded from 4.2-r15 to 4.2.2- r5 image. |
| FLCN-11298 | All | The misleading event was found when the mesh client was configured with static IP reconnects. |
| FLCN-11097 | All | AP was not getting the IP address through the USB LTE stick whenever the WWAN feature was enabled and the 3G dongle was connected. |
| FLCN-10214 | All | The connection via the Huawei E8372 USB LTE stick did not work. |