We offer two different schemes for wireless encryption on PTP 670:
- TLS-PSK
- TLS-RSA
TLS-PSK relies on an identical pre-shared key (PSK) installed in ODUs at both ends of the link. Ideally, the PSK is randomly generated, and unique to one link. The PSK provides authentication, authorization and privacy. AES encryption is based on the PSK.
In TLS-RSA we use X.509 certificates to authenticate the Master ODU to the Slave, and the Slave ODU to the Master. The subject of each certificate is the associated ODU’s MAC address. We authorize the remote ODU by checking the authenticated MAC address against the configured Target MAC Address, or against a whitelist or blacklist. AES encryption is set up based on a master secret established through the TLS negotiation. The ODUs can use a factory-installed device certificate, but they also support user-created certificates. The procedure set out below shows how to use OpenSSL to generate suitable user-created device certificates for TLS-RSA…
This procedure is similar to the recipe for certificates for HTTPS, except that here the subject is the MAC address, and not the IP address or DNS name. See this topic for the HTTPS certificates:
The HTTPS and device certificates are signed by a local Certification Authority, so also refer to this topic:
Okay, let’s get started…
First, generate the private key:
openssl genrsa -out 0004565800B8-key.pem 2048
Generate the certificate signing request:
openssl req -new -sha256 -subj "/C=GB/ST=Devon/L=Ashburton/O=Aardvark Enterprises/OU=Wireless/CN=0004565800b8" -key 0004565800B8-key.pem -out 0004565800B8-csr.pem
Note that we need to use lower case alphabetical characters in the CN field
Sign the request:
openssl x509 -req -days 3650 -in 0004565800B8-csr.pem -CA aardvark-ca-cert.pem -CAkey aardvark-ca-key.pem -CAcreateserial -outform DER -out 0004565800B8-cert.der
Finally, convert the private key to DER:
openssl rsa -in 0004565800B8-key.pem -outform DER -out 0004565800B8-key.der
The generated device certificate has the MAC address as the subject:
The device certificate forms a chain with the CA certificate:
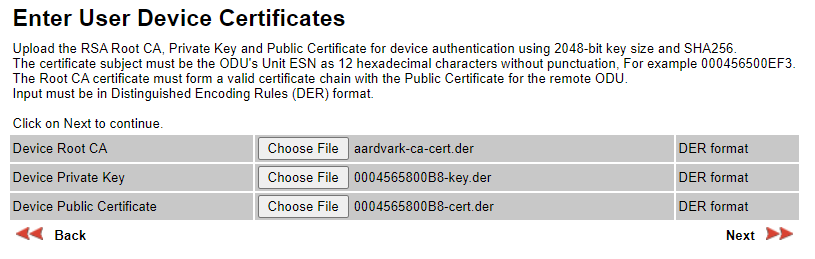
Install the Root CA, Private Key and Public Certificate in the ODU using the Security Wizard, like this: