Introduction
This document explains the procedure for configuring TACACS+ Authentication and implementing role-based access control for cnMaestro On-Premises, using the internal user groups from Cisco ISE.
Requirements
We recommend that you have knowledge of these topics:
- cnMaestro On-Premises Role Based access
- Cisco ISE TACACS Authentication and Authorization
- Cisco ISE Identity Management
- Connectivity between cnMaestro and ISE
Components Used
The information in this document is based on these software and hardware versions:
- cnMaestro On-Premises installed on VMware ESXi version 7.0.3
- cnMaestro On-Premised version 5.2.0.-r3
- Cisco ISE installed on VMware ESXi 7.0.3
- Cisco ISE version 3.3 with Patch 4
Configuration
Cisco ISE configuration
Cisco ISE (Identity Services Engine) uses TACACS+ (Terminal Access Controller Access Control System Plus) as a device administration service, enabling centralized authentication, authorization, and accounting for network devices. It facilitates granular control over device administrator access, allowing for selective roles /command authorization and audit logging.
The steps below configure the Cisco-ISE server for TACACS authentication to be used by cnMaestro On-Premises for role-based access.
TACACS User Groups
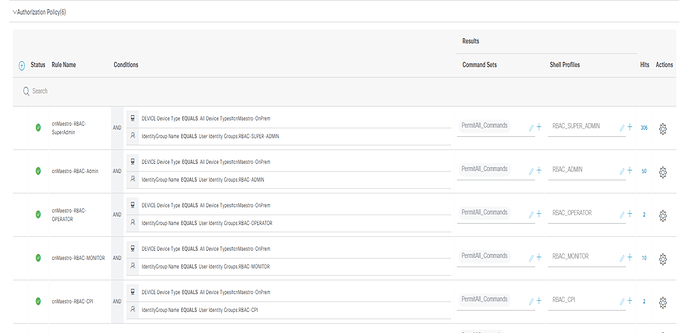
Below TACACS User Groups have been created in ISE for cnMaestro On-premises Role based access for different administrative roles
• Super Administrator role: RBAC-SUPER-ADMIN
• Administrator role: RBAC-ADMIN
• Operator role: RBAC-OPERATOR
• Monitor role: RBAC-MONITOR
• CPI role: RBAC-CPI
Steps for Creating the TACACS user group:
Navigate to Administration – Identity Management – Groups – User Identity Groups – click “Add”
Enter the Group information as below:
Group Name: Enter the preferred group name (ex: RBAC-SUPER-USER) and click on “Save”
TACACS Users
Below TACACS users have been created for different user administrative roles
• Super Administrator role: super-user
• Administrator role: admin-user
• Operator role: operator-user
• Monitor role: monitor-user
• CPI role: cpi-user
Steps for Creating the TACACS user:
Navigate to Administration – Identity Management – Identities – Users – Add user
Enter the user information below:
- Username: Enter the preferred username (This will be login username to cnMaestro On-premises)
- Password Type: Internal users
- Login Password: Enter the Preferred Password
- User Groups: select user group based on administrative role (RBAC-SUPER-ADMIN / RBAC-ADMIN / RBAC-OPERATOR / RBAC-MONITOR / RBAC-CPI ) – Click on: ”Save”
TACACS Profiles
Below TACACS profiles have been created for cnMaestro Role based access for different administrative roles.
RBAC: Super Admin Role:
Profile Attributes: role=SUPER-ADMIN-TEST
RBAC: Admin Role:
Profile Attributes: role=ADMIN-TEST
RBAC: Monitor Role:
Profile Attributes: role= MONITOR-TEST
RBAC: Operator Role:
Profile Attributes: role=OPERATOR-TEST
RBAC: CPI Role:
Profile Attributes: role=CPI-TEST
Network Device Profile
Navigate to Administration – Network Resources – Network device Profiles – click Add
Name: Cambium
Supported Protocols:Enable TACACS+
Network Device Group
Below network device Groups have been used:
- Device Profile: cambium
- Location: All Locations#India#Bengaluru
- Device type: All Device Types#cnMaestro-OnPrem
TACACS Protocol selection
Navigate to Work Centers – Policy Elements – Results – Allowed Protocols
Policy Sets
Below Policy set have been configured using device location location and device type groups.
Authentication Policies
Below authentication policies have been configured using ISE internal users.
Authorization Policies
Below authorization policies have been configured to authorize the network user.
cnMaestro configuration
Role-Based Access
Each user is assigned a Role that defines their authorization. On successful authentication, every request from this user is processed considering their Role. cnMaestro supports the following user Roles:
- Super Administrator: Super Administrators can perform all operations.
- Administrator: Administrators can modify cnMaestro application functionality, but they are not able to edit User, API, or Server configuration.
- Operator: Operators can configure device-specific parameters and view all configurations.
- Monitor: Monitors have only view access.
- CPI: CPI can onboard devices using the CBRS tool.
Configure TACACS server in cnMaestro On-Premises
Navigate to Administration – user – Authentication – External – click on “Add new”
Enter the details as below mentioned:
- Authentication Server Name: ISE
- IP Address/Hostname: ISE server IP address (XXXX)
- Port: 49
- Shared Secret: XXXXX (Preferred)
- Service Name: Enter preferred service name (Ex: cnMaestroRole)
Role Mappings used example:- Super Administrator: SUPER-ADMIN-TEST
- Administrator: ADMIN-TEST
- Operator: OPERATOR-TEST
- Monitor: MONITOR-TEST
- CPI: CPI-TEST
Authentication Priority
After adding the TACACS Authentication server to the on-premises server, select the authentication priority to configure and enable TACACS authentication as the primary login method for cnMaestro On-premises login. Please follow the steps below to configure the Authentication Priority:
Navigate to – Administration – users – Authentication – External – <Authentication Priority: Primary
Verify cnMaestro RBAC TACACS login:
Verify RBAC: Super Admin Role
Login to the cnMaestro GUI using the username:super-user as mentioned in this example
Verify RBAC: Admin Role
Login to the cnMaestro GUI using the username admin-user as mentioned in this example.
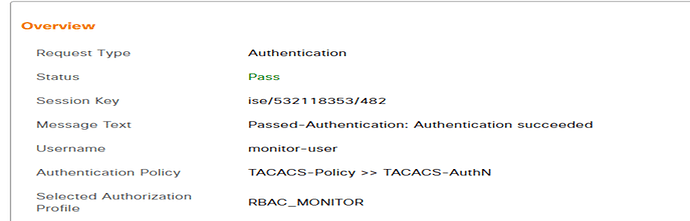
Verify RBAC: Monitor Role
Login to the cnMaestro GUI using the username:monitor-user as mentioned in this example.
Verify RBAC: Operator Role
Login to the cnMaestro GUI using the username:operator-user as mentioned in this example.
Verify RBAC: CPI Role
Login to the cnMaestro GUI using the username:cpi-user as mentioned in this example.
Troubleshoot
-
Unable to login to cnMaestro On-premises with TACACS login and Local user due to configuration issues
- If this configuration is unsuccessful, you may proceed to initiate a failover from ISE by removing the IP address of cnMaestro on-premises. This action will result in ISE not responding to the cnMaestro on-premises server, thereby allowing login to the on-premises server using local credentials.
-
Unable to login to cnMaestro On-Premises with error: “login failed, please check your credentials”. However, the Authentication and Authorization status in ISE is showing as successful.
- ISE shows successful authentication and Authorization is matching the correct rule however cnMaestro is still rejecting the request. You may wish to double-check the attributes that are configured correctly in the profile and no additional attributes are being sent.
cnMaestro expects a certain role or attribute value (like role=SUPER-ADMIN-TEST), and it’s not being received or matched properly, login fails.
- ISE shows successful authentication and Authorization is matching the correct rule however cnMaestro is still rejecting the request. You may wish to double-check the attributes that are configured correctly in the profile and no additional attributes are being sent.