PTP 650 and PTP 670 provide some really robust security features. The HTTPS interface for secure web management requires externally-generated private keys and public key certificates. If you’re working in a large organization, it’s very likely that you have access to a network security team that can generate this cryptographic material. In this case, leave it to experts. The basic requirements for keys and certificates are in the PTP 670 User Guide, or here: HTTPS in PTP 650/670 - Keys and certificates.
Not everybody has access to security specialists, and several security-conscious customers have requested additional detailed procedures for generating the necessary cryptographic material. In this topic, we describe one way to generate the necessary local Certificate Authority (CA) used to sign individual certificates for each ODU operated by the fictitious Aardvark Enterprises. We’re using the ubiquitous open source Open SSL software. Examples here are based on Open SSL version 1.1.1k.
The first step is to generate a 2048-bit RSA private key in the PEM format. We’re going to save the key in file example-ca-key.pem. Choose your own file name here. Here’s the Open SSL command:
openssl genrsa -out aardvark-ca-key.pem 2048
The second step is to generate a self-signed CA certificate based on this private key. Here’s the necessary Open SSL command:
openssl req -x509 -sha256 -days 3650 -subj "/C=GB/ST=Devon/L=Ashburton/O=Aardvark Enterprises/OU=Wireless/CN=Aardvark CA" -key aardvark-ca-key.pem -out aardvark-ca-cert.pem
This creates a certificate that is valid for 3650 days (about 10 years). Substitute your own subject details in the command line as appropriate.
Note that the country code (GB in this example) must be from a list of allowed codes. This list is based on the ISO 3166 two-letter series. This means that (for example) “US” is allowed, but “USA” is not allowed.
Windows wants to see a trusted Root CA certificate in the DER format, so we can convert the certificate to DER format like this:
openssl x509 -in aardvark-ca-cert.pem -outform DER -out aardvark-ca-cert.der
The CA certificate in this example is now saved as aardvark-ca-cert.der.
At this stage of the proceedings, save the private key securely; security of the HTTPS scheme depends on this remaining private. Don’t lose it though, because you’ll need the private key from time to time to sign the individual ODU certificates.
Install the CA certificate as a Trusted Root CA on all the management platforms that will be used for HTTPS with your PTP 670 ODUs.
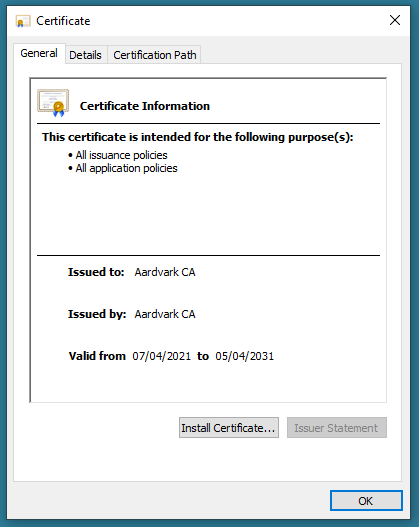
If this is all successful, you should be able to inspect the CA certificate in Windows like this:
Also, see:
Adding a Root CA Certificate in Chrome
Adding a Root CA Certificate in Firefox
Now check out how to generate the ODU certificates in Generate HTTPS Certificates for PTP 650/670 - Create ODU certificates